Ransomware Prevention: Essential Strategies, Incident Response, Trends for 2025, and Backup Best Practices
Estimated reading time: 12 minutes
Key Takeaways
- Ransomware attacks are surging, especially in critical sectors like manufacturing, healthcare, and energy.
- Implementing multilayered ransomware prevention strategies is essential to reduce risk.
- Effective incident response plans drastically improve recovery outcomes and reduce ransom payments.
- A strong backup strategy, especially following the 3-2-1 rule, minimizes data loss and downtime.
- Remaining aware of emerging ransomware trends for 2025 prepares organizations for evolving threats.
Table of contents
Ransomware prevention is now more critical than ever. Ransomware is malicious software that encrypts a victim’s data and demands payment for a decryption key. This threat is growing rapidly in the digital landscape. From January to September 2025, there were 4,701 ransomware incidents globally, a sharp increase from 3,219 during the same period in 2024. The rise has been especially apparent in critical sectors such as manufacturing, healthcare, and energy, which have experienced a 34% year-over-year increase in attacks. These alarming statistics confirm that ransomware prevention remains the primary line of defense against this costly cybercrime.
This blog post will explore four main areas: effective ransomware prevention methods, developing an actionable ransomware incident response plan, key ransomware trends expected in 2025, and creating a robust backup strategy to protect your data. By focusing on these areas, organizations can better protect themselves against evolving digital threats.
Source: Industrial Cyber Report
Understanding Ransomware and Its Impact
To design effective ransomware prevention techniques, it is essential to understand how ransomware operates and the severity of its impacts.
How Ransomware Works
Ransomware primarily enters systems through:
- Phishing emails: Malicious emails trick users into clicking infected links or attachments.
- Exploited software vulnerabilities: Attackers identify and exploit security gaps in outdated or unpatched software. Learn more about best practices
- Remote Desktop Protocol (RDP) weaknesses: Cybercriminals use brute force or stolen credentials to access systems remotely.
Once inside, ransomware encrypts files, making data inaccessible without a decryption key. Some ransomware variants also exfiltrate sensitive information, increasing pressure on victims by threatening public data leaks.
Consequences of a Ransomware Attack
The fallout from ransomware can be extensive:
- Massive financial losses: It is projected that ransomware will cost industries around $57 billion globally in 2025, averaging $156 million daily.
- Operational downtime: Recovery from attacks leads to significant operational disruptions, with average breach recovery costs of $7.42 million.
- Reputational damage: Data leaks and prolonged downtime damage trust and brand integrity. For example, Jaguar Land Rover faced a shutdown due to a ransomware attack, exposing wider national security concerns within critical sectors.
The combination of financial, operational, and reputational impacts makes ransomware a top priority for organizations worldwide, necessitating vigilant ransomware prevention and quick incident response. Explore cybersecurity trends
Sources:
Industrial Cyber Report
Mimecast Ransomware Statistics
Varonis Blog
Ransomware Prevention Strategies
Preventing ransomware infections requires a multilayered approach with a focus on closing vulnerabilities, hardening defenses, and educating users.
Patch Management
- Ensure all operating systems, software, and applications are updated promptly to close exploitable security gaps. Best practices for patch management
- Automatic patch management solutions speed up deployment and reduce delays that attackers exploit.
Employee Training
- Conduct ongoing training programs to teach staff how to spot phishing emails and suspicious links.
- Simulated phishing exercises improve awareness and reduce the risk of human error, which remains the primary ransomware entry point.
Endpoint Security
- Deploy comprehensive antivirus and anti-malware solutions on all network endpoints.
- Endpoint Detection and Response (EDR) tools add real-time threat monitoring to identify unusual behaviors that indicate ransomware. Explore top cybersecurity trends
Network Segmentation
- Divide networks into isolated segments to contain ransomware spread in the event of an infection.
- Restrict access controls and enforce the principle of least privilege to limit lateral movement by attackers.
Email Filtering
- Use advanced email filtering systems that block harmful attachments and known malicious URLs.
- This reduces the chances of ransomware entering through phishing campaigns or malware-laden emails.
Safe Browsing Habits
- Promote safe internet usage policies, such as avoiding untrusted websites and preventing drive-by downloads. Cybersecurity insights
- Platforms can enforce cascaded web filtering to block suspicious domains automatically.
Backup Strategy as Defense
- Complement prevention with a robust backup strategy.
- According to Mimecast, 64% of businesses successfully evaded ransom payments by relying on effective backups and incident response plans.
- Backups allow rapid restoration of encrypted or lost data without paying attackers.
Implementing these best practices forms a strong defense against ransomware, minimizing opportunities for infection and supporting quick recovery.
Source:
Industrial Cyber Report
Mimecast Ransomware Statistics
Developing a Robust Backup Strategy
A solid backup strategy is a critical pillar of ransomware prevention and recovery.
Key Components of an Effective Backup Strategy
- Frequent and Automated Backups: Regular, scheduled backups reduce the risk of data loss by narrowing the window during which data may be compromised.
- Offsite and Cloud Storage: Storing backups offsite or in cloud platforms protects against local data encryption or destruction. Cloud computing trends 2025
- Regular Testing: Testing restores backup data frequently ensures that backups are usable and that recovery processes are effective and timely.
The 3-2-1 Backup Rule
To maximize ransomware resilience, follow the industry-standard 3-2-1 rule:
- Maintain three copies of data.
- Use two different media types for storage (e.g., disk, tape, cloud).
- Keep one copy offsite or isolated from the primary environment to avoid simultaneous compromise.
This diversified approach safeguards backups from ransomware attacks targeting all copies at once.
Backup Strategy Reduces Impact
Reliable backups drastically reduce downtime and financial impact, accelerating recovery if prevention fails. However, data from Varonis shows that even after ransom payments, only 64.8% of healthcare organizations recovered their data fully. This highlights the importance of well-managed backups as a first line of recovery, avoiding ransom payments and lost data.
By integrating a dependable backup strategy, organizations reinforce their ransomware prevention efforts and improve business resilience.
Sources:
Mimecast Ransomware Statistics
Varonis Blog
Ransomware Incident Response
A swift and structured ransomware incident response can limit damage and ensure rapid recovery.
Immediate Response Steps
- Containment: Isolate infected systems promptly to prevent ransomware from spreading across the network.
- Eradication: Use forensic analysis to thoroughly remove ransomware and any associated malware.
- Investigation: Identify attack vectors and vulnerabilities exploited to improve defenses and prevent recurrence. DevOps best practices
Importance of a Tailored Ransomware Incident Response Plan
Having a specific ransomware incident response plan with defined roles and procedures is vital. Organizations with such plans have seen 64% success rates in overcoming attacks without paying ransom.
- This plan improves response speed and coordination.
- Clear steps for technical teams and stakeholders reduce confusion during high-pressure situations.
Communication and Legal Considerations
- Transparent communication with stakeholders, employees, customers, and the public helps manage reputation during attacks.
- Legal and regulatory compliance requires timely breach reporting, particularly in critical sectors such as healthcare and energy.
Preparedness through a robust ransomware incident response plan complements prevention efforts and supports effective recovery. Cybersecurity trends insights
Sources:
Industrial Cyber Report
Mimecast Ransomware Statistics
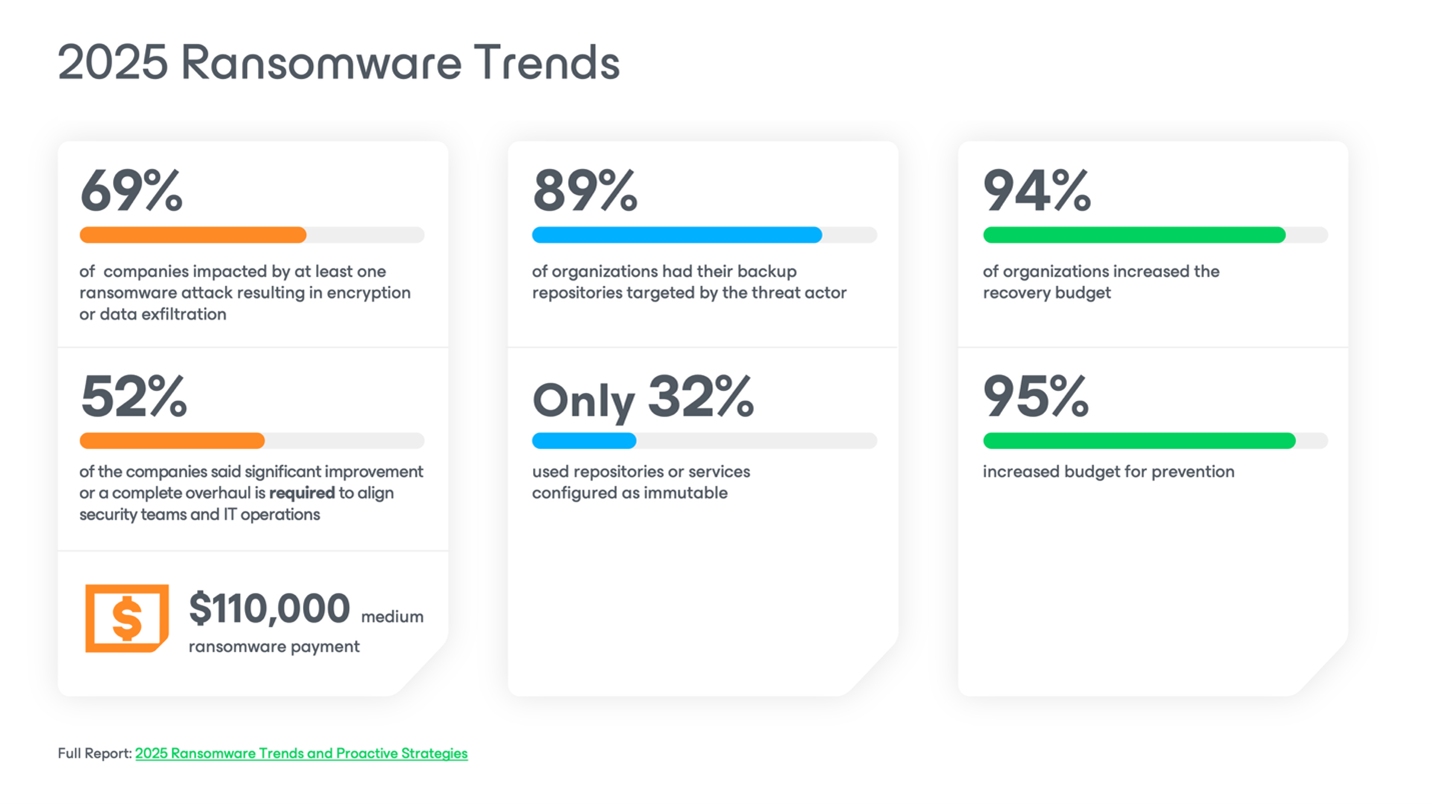
Ransomware Trends 2025
Understanding ongoing ransomware trends is essential for adaptive ransomware prevention and response strategies.
Critical Sectors Under Attack
- Half of all ransomware incidents in 2025 hit critical sectors.
- Manufacturing experienced a 61% surge in attacks, with 838 total incidents.
- Overall, attacks grew by 34% year-over-year.
Geographic and Group Dynamics
- The United States accounted for 21% of global ransomware cases.
- U.S. incidents spiked 149% early in 2025.
- Currently, 103 active ransomware groups operate worldwide.
- Five groups (Qilin, Clop, Akira, Play, SafePay) are responsible for 25% of attacks.
Professionalization and Consolidation
- Market consolidation continues, with 65 groups active by Q2 2025.
- This indicates increasing sophistication and possibly more targeted attacks.
Financial Impact and Defense Innovations
- Average ransom payouts range between $1 and $2 million.
- Despite a 35% downturn in total ransom payments in 2024 ($813.55 million), associated costs like downtime and recovery have risen.
- Emerging defense technologies focus on real-time network monitoring, AI-driven threat detection, and proactive cybersecurity approaches to stay ahead of attackers. Top cybersecurity trends
These trends highlight the dynamic ransomware landscape, emphasizing the need for updated and comprehensive ransomware prevention measures and incident response capabilities.
Sources:
Industrial Cyber Report
Exabeam Explainers
Varonis Blog
Rapid7 Q2 2025 Analysis
Conclusion
Ransomware prevention remains the frontline defense against the growing threat of ransomware in 2025 and beyond. Protecting your organization requires a multi-layered approach:
- Timely patch management to close vulnerabilities. Learn patch management best practices
- Continuous employee training to reduce phishing risks.
- Deploying endpoint security and network segmentation.
- Implementing comprehensive email filtering and promoting safe browsing habits.
- Developing and maintaining a solid backup strategy, particularly following the 3-2-1 rule. Cloud computing trends
- Preparing a tailored ransomware incident response plan to enable swift containment, eradication, and recovery.
Staying informed on ransomware trends for 2025—especially the sharp rise in attacks on critical sectors and the increasingly sophisticated ransomware groups—enables organizations to proactively adapt their cybersecurity postures. Cybersecurity trends insights
By implementing these strategies in unison, organizations can significantly reduce risk, protect their data, and maintain operational integrity against ransomware threats.
Sources:
Industrial Cyber Report
Mimecast Ransomware Statistics
Varonis Blog
Frequently Asked Questions
What is ransomware?
Ransomware is a type of malicious software that encrypts a victim’s data and demands payment, typically in cryptocurrency, to provide a decryption key for restoring access to the data.
How can organizations prevent ransomware attacks?
Organizations can prevent attacks by implementing patch management, employee training on phishing, endpoint security tools, network segmentation, email filtering, safe browsing habits, and maintaining robust backup strategies.
What is the 3-2-1 backup rule?
The 3-2-1 backup rule advises keeping three copies of data, stored on two different media types, with one copy kept offsite or isolated to protect against data loss or ransomware.
Why is a ransomware incident response plan important?
An incident response plan enables swift, coordinated action during an attack, limiting damage, accelerating recovery, and reducing the likelihood of paying ransom.
Which sectors are most targeted by ransomware in 2025?
The manufacturing, healthcare, and energy sectors are critically targeted, accounting for half of ransomware incidents in 2025, with steep increases in attacks year-over-year.

